TL;DR
At WebCamp Zagreb I attended Luka Kladaric excellent talk on HTTP Strict Transport Security Header (HSTS) Header. This talk and Q&A session at the end helped me to fully understand how this header works in practice. As a software tester, I will also provide tests that confirmed HSTS mechanics and heuristics why you should set up this header at your site.
The problem
Your site is hosted at environment that still supports HTTP protocol, for a number of reasons. One reason could be compatibility with legacy code of other customers that use same hosting environment. So killing HTTP port is not an option.
That means that POST request
http://www.tentamen.hr/contacts
with all form data
WILL make a roundtrip to white house server in PLAIN TEXT. Which is not good.
The solution
In order to block the browser to not make that request in plain text, HSTS Header is introduced. You set up following header on your site:
Strict-Transport-Security: max-age=31536000
which instructs browser to make LOCAL redirect (HTTP 307) directly to HTTPS url:
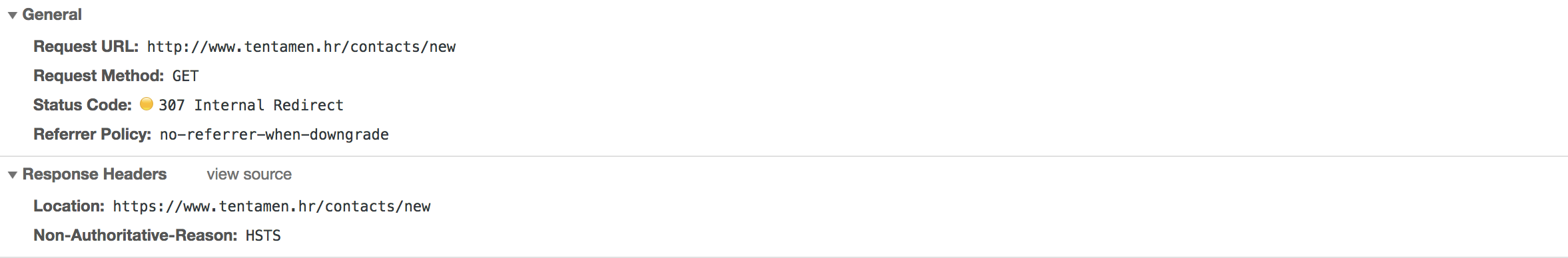
This will be enforced from now up to max-age number of seconds. HTTP 307 is local redirect, which means that no server round trip is made.
The ultimate security solution is to kill HTTP port. But if you are on Heroku, this is not possible, because you do not have that kind of control on Heroku platform. HSTS is supported by all modern browsers, so your only risk here is that your site is used by user that comes from the past :).
HSTS supports two more parameters:
includeSubDomains
This is combined with Set-Cookie header and it means that HSTS is enforced for all subdomains taking that main domain is one for which cookie is issued. Sounds complicated? Lets take for example my site. Set-Cookie for www.tentamen.hr does not have domain section, which means that cookie is only issued for www.tentamen.hr. And what are subdomains of www.tentamen.hr? For example, email.www.tentamen.hr.
So if you do not have subdomains of your site domain, you do not need to set this attribute.
preload
Use this if you want to send your domain to HSTS list maintained by Chrome. Your domain will be hardcoded for HTTPS only in that list. problem is if you would like to switch back to HTTP, it takes months to be removed from that list.
Here are my notes: