TL;DR
In this week’s reading club, we recommend About Public Key Pinning. This article is an example of why web security is very complicated.
What is Key Pinning about? If you have opened ssh connection, you got the message:
The authenticity of host ‘FreeBSD (10.0.0.4)’ can’t be established.
ECDSA key fingerprint is b0:79:74:0f:58:20:80:fd:c7:47:33:d6:9c:40:df:20.
Are you sure you want to continue connecting (yes/no)?
After you press yes, that message would not be shown again until the server changes its public/private key pair. With answering yes, you stored servers public key to your machine. You pinned that public key because you are sure that the FreeBSD server is safe because you trust the person who gave it access to that server.
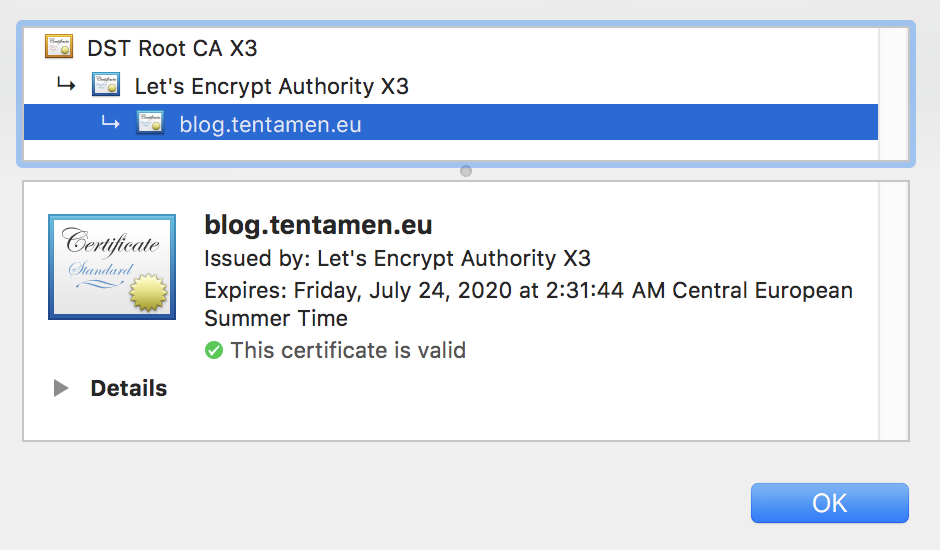
The idea is to apply key pinning to SSL public certificate. If you look at the image above, you can see that the certificate for this blog is issued by Let’s Encrypt. The problem is that any DST Root CA leaf can also grant valid blog.tentamen.eu certificate. Key pinning is a dangerous method where the client would only trust public keys of listed CA leaves listed in special header. Why is it dangerous? Because it is possible to forbid access to your site to all clients in the world.


